suricata使用
suricata命令行
1 | Suricata 5.0.9 |
我们按照suricata官网要求安装好之后,采用
1 | find / -name suricata |
可以
查看所有suricata路径,配置文件路径
1 | 打开 |
我们编辑时,因为我们知道我们的网卡名称可能并不是eth0,所以在af-packet 节需要匹配
在suricata.yaml中找到af-packet部分,进行如下设置
1 | af-packet: |
之后,
安装规则集
1 | sudo suricata-update |
规则安装在 /var/lib/suricata/rules 这也是配置中的默认设置,并使用 suricata.rules 文件。
安装了规则后,Suricata可以正常运行,因此我们重新启动它:
1 | sudo systemctl restart suricata |
我们注意,在QEMU的虚拟机中,安装好这一切后,可能启动suricata服务后,检查其状态时
1 | sudo systemctl status suricata |
发现其运行失败,这个并不用担心。
我们可以采用进程后台运行的方式
1 | suricata -c /etc/suricata/suricata.yaml -s /var/lib/suricata.rules -i eth0 -D |
即可后台运行,不占用终端。
我们可以采用
1 | ps -a#查看进程 |
再用
1 | kill -9 PID |
杀死进程。
或是用
1 | killall sshd(name) |
来杀死进程
我们开启进程后,执行了一些请求访问命令比如curl
1 | curl http://testmynids.org/uid/index.html#用于返回UID,GID等等 |
然后查看日志
有pcap文件的前提是我们把suricata.yaml中的允许生成pcap项设为了allow或是yes(我忘了)
我们查看其中一个
1 | cat log.pcap.1655036325 |
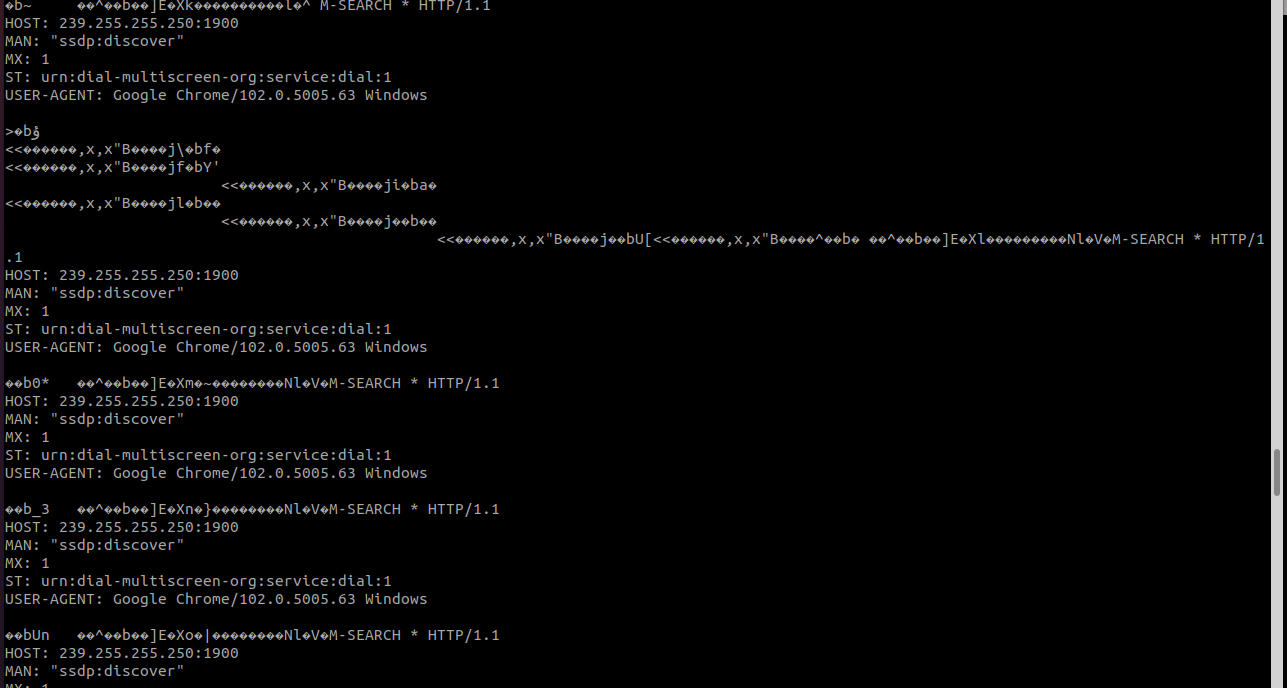
里面是流量。
可以了解一下ssdp用于网络发现
对于其格式,简要介绍一下
1 | M-SEARCH * HTTP/1.1 |
239.255.255.250为ssdp专用多播地址,1900为ssdp专用端口号
MAN后面的ssdp:discover为固定,MX为最长等待时间,ST:查询目标,它的值可以是:
upnp:rootdevice 仅搜索网络中的根设备
uuid:device-UUID 查询UUID标识的设备
urn:schemas-upnp-org:device:device-Type:version 查询device-Type字段指定的设备类型,设备类型和版本由UPNP组织定义。
其中,第三种一般可以用来自定义设备,如:ST: urn:schemas-upnp-org:device:Server:1
在设备接收到查询请求并且查询类型(ST字段值)与此设备匹配时,设备必须向多播地址239.255.255.250:1900回应响应消息。
————————————————
版权声明:本文为CSDN博主「CUC_Tony」的原创文章,遵循CC 4.0 BY-SA版权协议,转载请附上原文出处链接及本声明。
原文链接:https://blog.csdn.net/zhu530548851/article/details/28611657
我们看其他的日志
我们虚拟机开一会可能会在日志中看到很多信息,打印不完,因为我们后台一直运行着suricata这个进程!就像windows defender!
编写规则
我们编写过后的规则要加在
1 | /var/lib/suricata/rules/suricata.rules里面 |
我们可以先查看一下里面的规则,发现大部分都没有启用,都被注释,也就是我们启用时要先接触注释
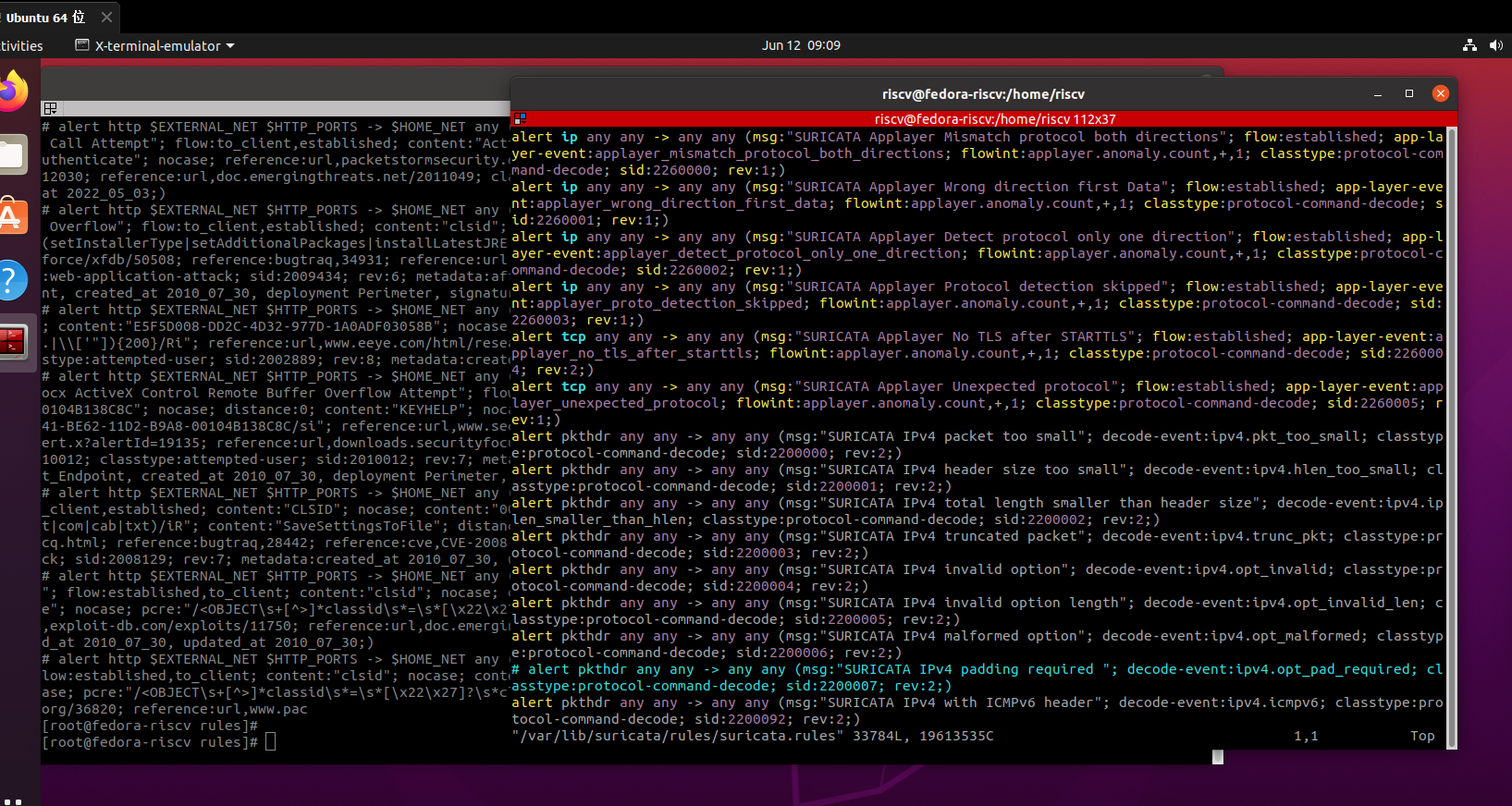
右边的带颜色的为每条规则。
示例如下:
1 | drop tcp $HOME_NET any -> $EXTERNAL_NET any (msg:"ET TROJAN Likely Bot Nick in IRC (USA +..)"; flow:established,to_server; flowbits:isset,is_proto_irc; content:"NICK "; pcre:"/NICK .*USA.*[0-9]{{3,}}/i"; reference:url,doc.emergingthreats.net/2008124; classtype:trojan-activity; sid:2008124; rev:2;) |
drop为action
tcp $HOME_NET any -> $EXTERNAL_NET any为header
(msg:"ET TROJAN Likely Bot Nick in IRC (USA +..)"; flow:established,to_server; flowbits:isset,is_proto_irc; content:"NICK "; pcre:"/NICK .*USA.*[0-9]{{3,}}/i"; reference:url,doc.emergingthreats.net/2008124; classtype:trojan-activity; sid:2008124; rev:2;)为options
action:
1 | Valid actions are: |
header里面的protocol段
tcp (for tcp-traffic)
udp
icmp
ip (ip stands for ‘all’ or ‘any’)
还有一些其他的
http
- ftp
- tls (this includes ssl)
- smb
- dns
- dcerpc
- ssh
- smtp
- imap
- modbus (disabled by default)
- dnp3 (disabled by default)
- enip (disabled by default)
- nfs
- ikev2
- krb5
- ntp
- dhcp
- rfb
- rdp
- snmp
- tftp
- sip
- http2
这些协议是否能使用,要看suricata,yaml中的配置是否允许。

